If you are an engineer or developer responsible for building embedded systems (or software, equipment, networks, etc.), then one of your highest priorities is (or should be) identifying and minimizing potential Data security breaches. To achieve this goal effectively, you need to understand how the system is hacked, and ultimately how to "think like a hacker".

Hackers exploit vulnerabilities, which may be design flaws, weak access control, configuration errors, or many other problems. This article will delve into the thinking of hackers. As you can see, their process and way of thinking in discovering and exploiting vulnerabilities is quite different from how engineers deal with system development.
What is the thinking of hackers? The following content may be interesting, confusing or boring, so prepare a large cup of coffee for us to delve into it.
Hacker's mentality and thinking: carrying out tasksThe most significant difference between hackers and engineers is how they respond to challenges. Engineers (and scientists, for that matter) are systematic. They first define and analyze the problem, then make a plan (or hypothesis), and test the hypothesis. Finally, analyze the test results and draw conclusions regardless of success or failure.
This is a scientific method. People have adopted this process for hundreds of years, and hackers will not follow this process. First of all, there is no plan, but as a task. Hackers' plans are uncertain and flexible. Remember that hackers are not building projects that must pass the test of time. Instead, what they have to do is crack. They don't need to satisfy the manager or CEO, they are concerned with completing the defined tasks.
Engineers do things systematically, while hackers are pragmatic, and their methods are very practical. Although there will be some similarities, the core difference is that hackers will do their best to complete their tasks. In addition, they will not pay attention to results that are not helpful to them, and they do not need to explain to others.
This is sometimes described as list vs. path thinking:
• Scientists and engineers report results for each item listed
• Hackers follow the path, they will continue on one line of thought, knowing that the path will not work
All in all, the goal of engineers is thoroughness, and the goal of hackers is effective. These seemingly small nuances will show huge differences and impact once they are implemented.
Common pattern: kill chainWhen hackers intrude into an environment or system, they usually follow a common pattern called kill chain. When hackers attack the system and network, they will look for higher-level access in the environment And operating permissions (Figure 1). Finally, when they gain sufficient access rights, they can steal the data they want or plant malicious code.
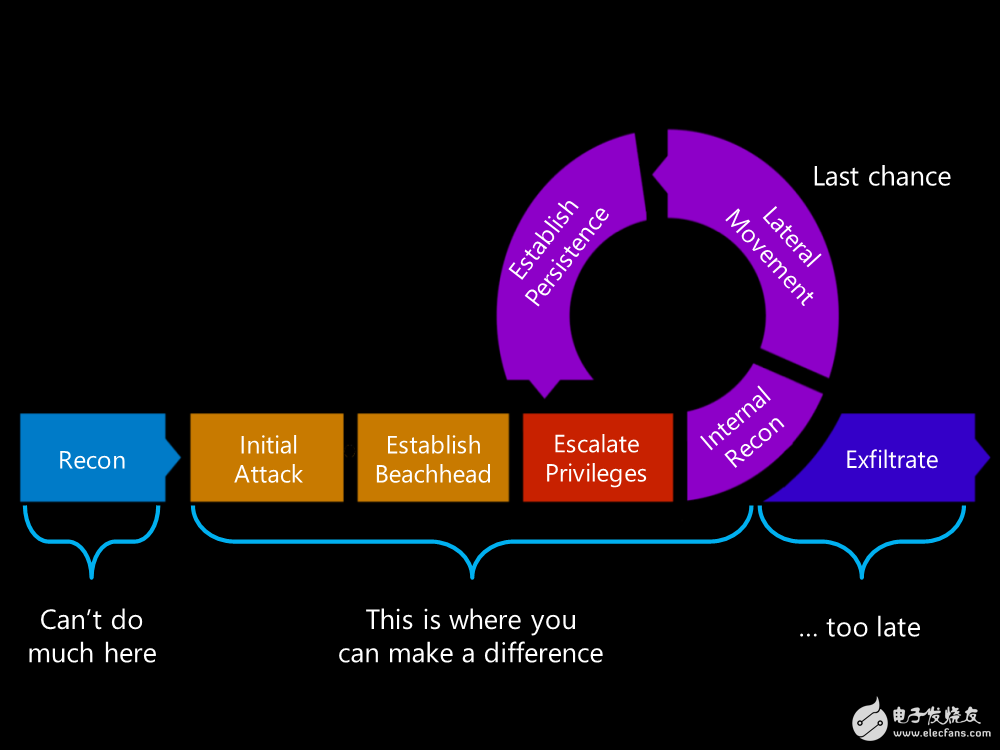
Figure 1: If you can catch hackers early in the kill chain, then you can prevent hacker attacks from happening
Hackers often stay in an intrusion environment for a long time: an average of 100-140 days. For example, a retail chain company encountered a hacker attack in 2013. Hackers spent about 100 days in a full-scale attack. If you can kill Early detection of hackers in the chain can prevent hacker attacks from happening.
It should be noted that most hacking attacks are done automatically using robots. Although we can describe that the actual execution of these operations is artificial, it is actually the robot that completes all the operations behind it.
Hacker thinkingHackers see things from different perspectives, especially the following points:
• Observe obvious details
• Imagine the worst
• Explore every potential entrance
• Like all data
• Understand that people are the weak link
• Like obscure information
• Find and use backdoors
• Exploit third-party vulnerabilities
• Seek credentials
• Clean up garbage
Observe the obvious detailsIt’s easy to overlook an obvious weakness when you go deep in your development. You might as well take a step back and ask yourself some basic questions. Use the following "five whys" to evaluate:
• Why does your product do this?
• Why is this necessary?
• Why use this design method?
• Why is this good?
• Why not change it in a different way?
• The purpose of this exercise is to find the obvious weaknesses. Hackers will find them, much faster than you think.
Imagine the worstWhat is the worst case? How likely is it to happen? Hackers generally have no moral standards. When your network or application is mired in a quagmire and trying to recover, they will not feel sympathy, so you need to make a plan to deal with those worse situations.
However, be careful not to get involved in the so-called "zombie scene", which is a disaster caused by a series of absurd events. Most zombie movies are based on this premise.
Explore every potential entranceYou must know every possible way for anyone or anything to access your system. Hackers will make all the attempts, many times. You may think that your Bluetooth interface is super secure, but there are dozens of ways to specifically use Bluetooth to make your system insecure. Make sure that you actively test each interface, regardless of your system design. How complicated.
Like all dataHackers prefer data or certain types of data. Data storage is also a way for hackers to gain persistent access in the environment. You must analyze your system data:
• How is the data stored?
• How is the data transferred?
• Who can access this data?
• How to monitor, manage and control access to data?
• What is the access log? Where did all this data go?
Understanding that people are the weak linkHackers understand that people are the weak link in data security. We are not only unstable and unreliable, but also extremely vulnerable to manipulation. If your system involves anyone with these weaknesses (he does have these weaknesses), then this is your system Weakness.
All information security issues usually boil down to human weakness. Regardless of whether we have made the wrong configuration or written the wrong code, people create some weaknesses in the system. Assuming that users will make mistakes, and there will be many mistakes, so we have to pay special attention to some human operations.
Like obscure technical informationHackers like obscure technical information. They will randomly dig out documents that you have stored a few years ago, and use the data of these documents to attack your system. This is also one of the joys of cracking new systems.
Be cautious when you release certain types of technical data to the public, assuming that hackers will get it and analyze it. If your product is developed in an open environment, then you should design certain types in a more secure way. Components and functional characteristics.
Find and use backdoorsA movie "War Game" in the 1980s made many hackers experience the taste of hacker attacks. There is a great scene in the middle of the movie. A computer scientist blames his nerd colleague for using the backdoors of the computer system as secrets: "Mr. Potatohead, these backdoors are not secrets!"
His words seem to be as true now. The backdoors of applications or devices are very common, and hackers will look for them. It is one of the oldest and most reliable technologies for hacking into the system. It is shown in "Game of War". Of course it still applies today.
Exploit third-party vulnerabilitiesAlthough you may be deeply concerned about the security of the system, does your supplier or partner also care about the same as you? Hackers usually target third-party components, because a large number of related targets can be attacked by acquiring a certain technology. Heartbleed is an example of system risks caused by insecure third-party components. Heartbleed is a flaw in the design and implementation of OpenSSL. OpenSSL is applied to millions of products, which means that one vulnerability is enough to cause millions (maybe dozens of 100 million) devices were attacked.
If your system is integrated with a third-party component, it will inherit all the weaknesses of that component. Although the product may belong to others, you need to be responsible for its security issues.
Find credentialsLegitimate user accounts are ultimately what hackers want to obtain. Once they obtain the credentials, the hackers will upgrade their permissions to gain access to your system. In addition, using legitimate credentials usually does not trigger an alert.
Although you may not always be able to protect the user’s credentials (because it is in the user’s hands), you can still prevent malicious use of these credentials. This starts with the implementation of minimal permissions, which means that users can never have more than they need. Access permissions, in addition, you should actively test the system for access escalation attacks.
Clean up your trashIs your system part of the whole? When one part is attacked, other parts will also be attacked? What happens if you pass false data to your system? This is how the Stuxnet malware works. It will provide false information to the industrial control system and overload the system. If hackers want to steal your data or perform sabotage operations, it may overload your system like excessive network traffic.
Denial of service attacks are difficult to prevent. When designing your system, you need to consider whether it may be overloaded, and establish a corresponding mechanism to prevent or ignore a large amount of input data. In addition, the clock needs to verify the data sent to your system. Whether the data is trustworthy or not is very important.
to sum upAs a design engineer, identifying and minimizing potential data security vulnerabilities is the main goal. Hackers work very differently from engineers. They do not adopt a systematic approach. They have their own kill chain method. In this way, they will continue to find vulnerabilities to exploit. "Think like a hacker" requires you to look at the system you design in a different way. Part of it means understanding the technical details of the vulnerabilities and solutions. The more important part is to observe some obvious flaws, understand some of the mistakes and omissions that people make, understand what hackers are looking for and how they use these clues.
An electrical appliance used to protect electrical equipment from high transient overvoltage hazards and to limit the duration of continuous flow.This term includes any external clearance necessary for the normal functioning of the appliance during operation and installation, whether or not it is a unit as a whole.
Surge protector, also known as lightning arrester, is an electronic device that provides safety protection for all kinds of electronic equipment, instruments and communication lines.When the electric circuit or communication lines or for outside disturbance suddenly produce peak current in voltage, surge protector in a very short time conduction tap, to avoid surge damage to other devices in the circuits.[1]
Surge protector, suitable for ac 50/60 hz, rated voltage 220 v to 380 v power supply system, the indirect lightning and thunder and lightning directly affect transient over voltage surge protection, or other applicable to the family home, the third industry and the surge protection industry requirements.
Surge Protector,Surge Voltage Protector,Eco-Friendly Surge Protector,Lightning Protection Surge Protector
YANGZHOU POSITIONING TECH CO., LTD. , https://www.cnchipmicro.com